KeyRings
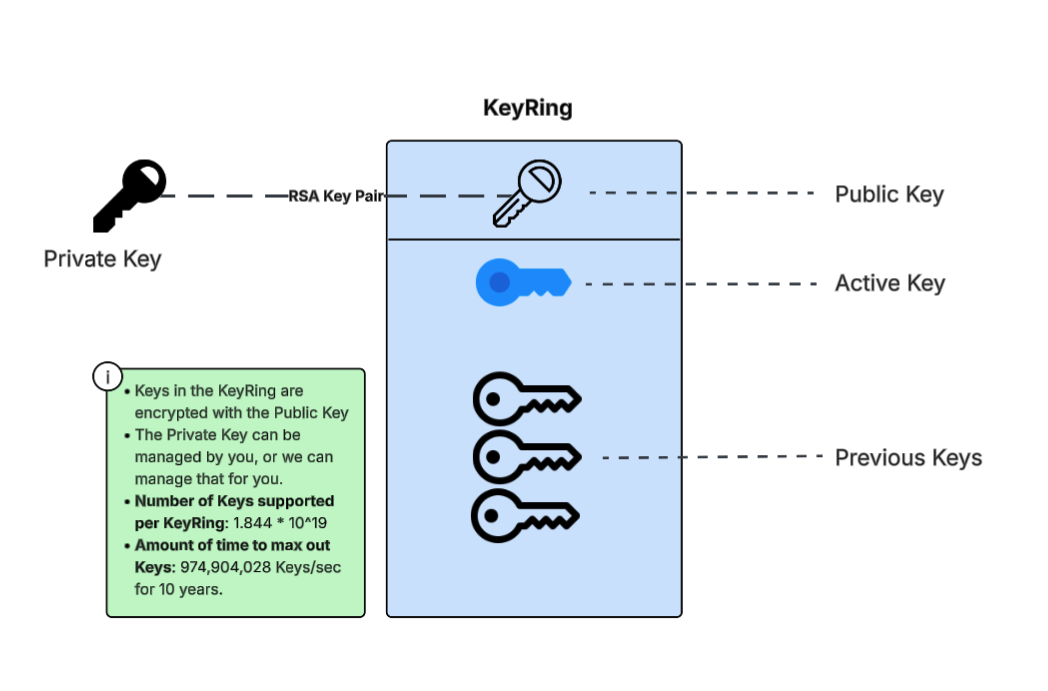
KeyRings organize collections of Keys and offer a structured way to separate them across logical groups. When a KeyRing is created, it receives a unique name along with a Public Key from an RSA 4096-bit Key Pair. Every Key added to the KeyRing is encrypted using this Public Key, which means that anyone holding the corresponding Private Key can decrypt it.
Grizzly can handle the generation and management of these Key Pairs on your behalf. Alternatively, you can supply and manage your own, a setup known as Customer Managed Keys.
KeyRings consist of several parts:
- Active Key: There is always 1 Active Key on a Keyring
- Unique Name: A string based name provided when the KeyRing is created
- Configuration: Configuration of the KeyRing's behavior
- ID: Unique ID for the KeyRing
Active Key
When a KeyRing is first created, a Key is also created and made to be the Active Key. KeyRings track all encrypt calls, and, based on configuration, will automatically rotate the Key for you, replacing the previous Active Key. Once a Key has been rotated, it is never used again for encrypting.
KeyRing Creation
To create a Keyring, the following are required:
- Unique Name: Unique name of the KeyRing
- Public Key: PEM encoded, Public Key of an RSA-4096 bit Key Pair
When a KeyRing is first created, a Public Key, of an RSA 4096-bit Key Pair, is provided. Grizzly can manage these Key Pairs or you can provide your own. The Private Key will need to be available to decrypt a Key when it is requested from the Key Ring.
How To Create an RSA Key Pair Using openssl
openssl genrsa -out pem 4096
openssl rsa -in pem -pubout -out pem.pub
When a Key is rotated, and a new Key created, the Key Ring encrypts the new Key with its Public Key before it is stored. Grizzly never saves an unencrypted Key.
KeyRing Naming Requirements
KeyRings must have a unique name within the platform, and may contain any characters except: "':;!@#$%^*() =+{}[]|?\/><.,. Although there is no restriction on the name length, it is recommended to keep it 64 characters or less to help manage them.
KeyRing Configuration
KeyRings have the following configuration:
{
"config": {
"props": {},
"key": {
"props": {
}
},
"algos": {
"aes256": {
"maxEncryptCount": 10000
}
}
}
}
props: Metadata on the KeyRing itselfkey.props: These props are copied to Keys when they are created. When this value is changed, new Keys will adopt the new values.algos: This object represents the unique algorithm configuration per supported algorithm. AES256 is the currently supported algorithm.algos.aes256: Configuration related to AES256 encryption.maxEncryptCount: The number of times a Key is used before rotating to a new Key. We recommend tuning this value based on the size of the data that is being encrypted. Ideally the Key is rotated when 64gb of data has been encrypted with a Key.